Hackers proceed to present consideration to known assistive application vulnerabilities
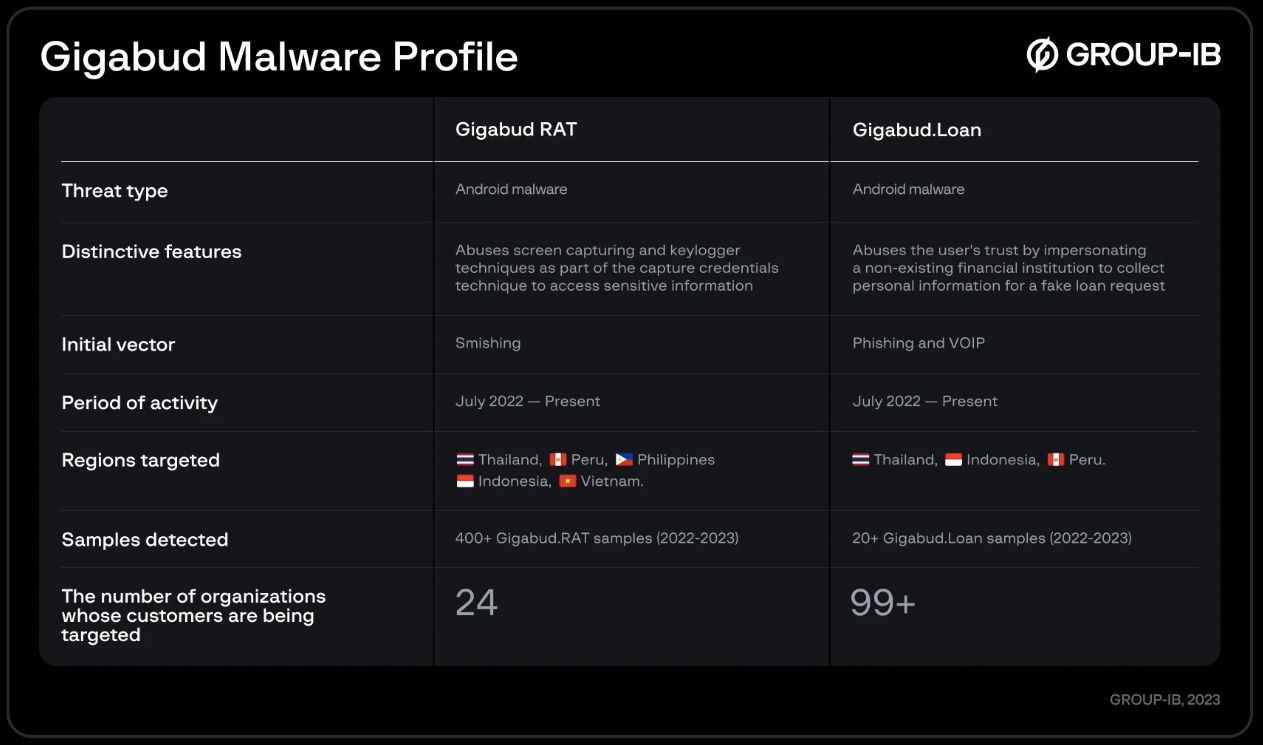
Malware has proven to a blessedly dinky but silent power-as-a-mosquito subject on Android. Hackers many times target known dilapidated capabilities within the working machine to rob wait on of users, and more in total than no longer, accessibility application is exploited. Now not too long within the past, cybersecurity researchers Crew-IB bear attributed a spate of financially-driven hacks all over Southeast Asia and Central The us to the Gigabud Random Get entry to Trojan (RAT), on Android devices.
This malware first seemed in Thailand, in step with Crew-IB’s newest list. In July 2022, Thai Android users got emails and SMS messages that linked to a faux model of Thai Lion Air’s web station. The baited users downloaded malicious application, licensed it to rating admission to their devices and granted it completely different permissions in enlighten to qualify for a loan. Gigabud RAT variants incentivize users to download the malware in completely different programs in completely different contexts, but the Thai Lion Air case illustrates the fundamental system.
Unsurprisingly, data the users submitted to the faux web station didn’t run to Thai Lion Air. As a replace, that went to a server bound by the of us who circulated the Gigabud RAT malware. Russian hackers deployed a the same data-syphoning machine closing one year. Once assign in, such malware can construct better than relay data. Due to hooking in to Android’s accessibility services, the applying can stealthily work alongside side other apps, harvest data from them, and even mess with what that it is doubtless you’ll perhaps presumably also bear purchased saved to the clipboard.
Importantly, this malware doesn’t construct anything inappropriate except after employ and accessibility permissions are granted, making it advanced to watch. Once assign in, Gigabud RAT malware can largely work alongside side your telephone’s application as must you bear been doing it your self, opening the door for exploits with authentication or even transferring funds.
Given all of this advanced functionality, faulty actors utilizing Gigabud RAT to perpetrate frauds are inclined to desire passive data gleaning ways to salvage sensitive data the put that that it is doubtless you’ll concentrate on of, similar to keystroke logging and camouflage recording. This, too, minimizes detectability.
Crew-IB reviews detecting over 400 situations of Gigabud RAT within the wild, filled with life in over 100 nations. Threat actors bear deployed it in schemes to impersonate over 25 companies and executive companies. These findings signify a startling development price and geographic spread since researchers first known the decided Gigbabud malware household closing one year.
Android 14 will upgrade the protection of the Accessibility API, which must silent construct the vogue of safety breaches completed by malware delight in the Gigabud RAT, Nexus, and Cereberus more advanced. Google Play recently pulled the iRecorder Cloak Recorder app from the Play Store attributable to associated vulnerability concerns. With any luck better scanning ways wait on defend apps delight in that far from users within the first residing.