Summary
- WhatsApp is centered on privateness and uses open-supply encryption straightforward programs to stable consumer conversations.
- The most contemporary beta replace automates the encryption online page verification direction of, placing off the need for manual intervention.
- For this, WhatsApp is imposing a unusual key transparency scheme to within the sever fee of the strain on its servers and streamline security verifications.
Privacy is crucial to our online actions, and in particular so in deepest conversations. WhatsApp is idea of as among the most well-liked encrypted messaging apps on hand on Android, and Meta developers gradually reiterate the app’s center of attention on privateness. The firm uses open-supply encryption programs and is somewhat clear relating to the implementations, too. Then once more, all these aspects mean puny to WhatsApp users within the event that they cannot take a look at the encryption in amble. For this, the developers incorporated a utility allowing you to convey the encryption online page of a chat manually. Now, the most contemporary beta replace is automating this encryption verification direction of, so it doesn’t need your intervention.
WhatsApp uses halt-to-halt encryption (E2EE) for all its messages, media, and aspects, for the explanation that feature’s rollout in 2016. WhatsApp white papers indicate particular individual messages are encrypted on the Signal Protocol (no longer to be at a loss for words with a messaging app by the identical title), which is an open supply protocol you presumably can audit on GitHub. No matter the transparency this brings, your chats with a individual cannot be compromised since the message is encrypted for your application, and handiest the supposed recipient would have the supreme cryptographic key to decrypt it. The scheme ensures no one else can decode the message — no longer even WhatsApp itself.
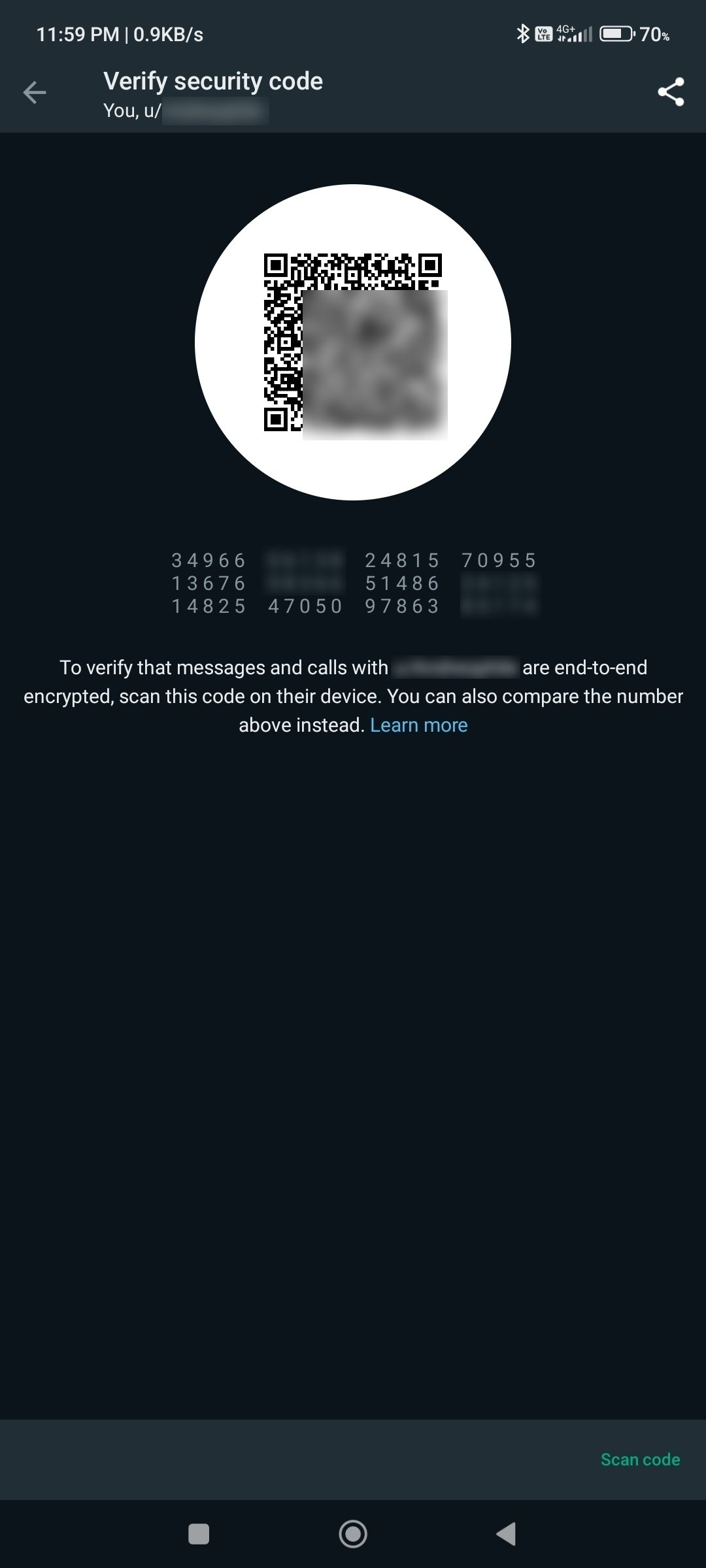
Alternate choices for the time being on hand for security verification within the stable version
Even supposing these cryptographic keys are refined strings, WhatsApp uses concatenation and mathematical operations to within the sever fee of them to 60-digit codes, spoil up into chunks of 5 for readability. This code is weird for each conversation and likewise varies by application. That’s potentially because linked gadgets now keep in touch straight with WhatsApp servers rather than routing messages via the well-known cell telephone. In neighborhood chats, each pair of participants shares a explicit key. Even supposing each WhatsApp message has a explicit cryptographic key, the toughen documentation also unearths the 60-digit code won’t switch while you send a message.
To lunge wanting this concatenated code for manual verification, you presumably can open any chat, then faucet the contact title → Encryption. The section also has a QR code which your contact can scan the exercise of their application to convey encryption. If the 60-digit code doesn’t match, or the QR code scan fails, it must be indicative of a individual-in-the-center attack, otherwise you can also very properly be checking the code for the mistaken chat. Here’s a gradual manual direction of, no matter the exercise of a QR code. Support in April, WhatsApp promised to automate this feature while asserting two other crucial security-linked changes which had been speculated to lunge reside in subsequent months.
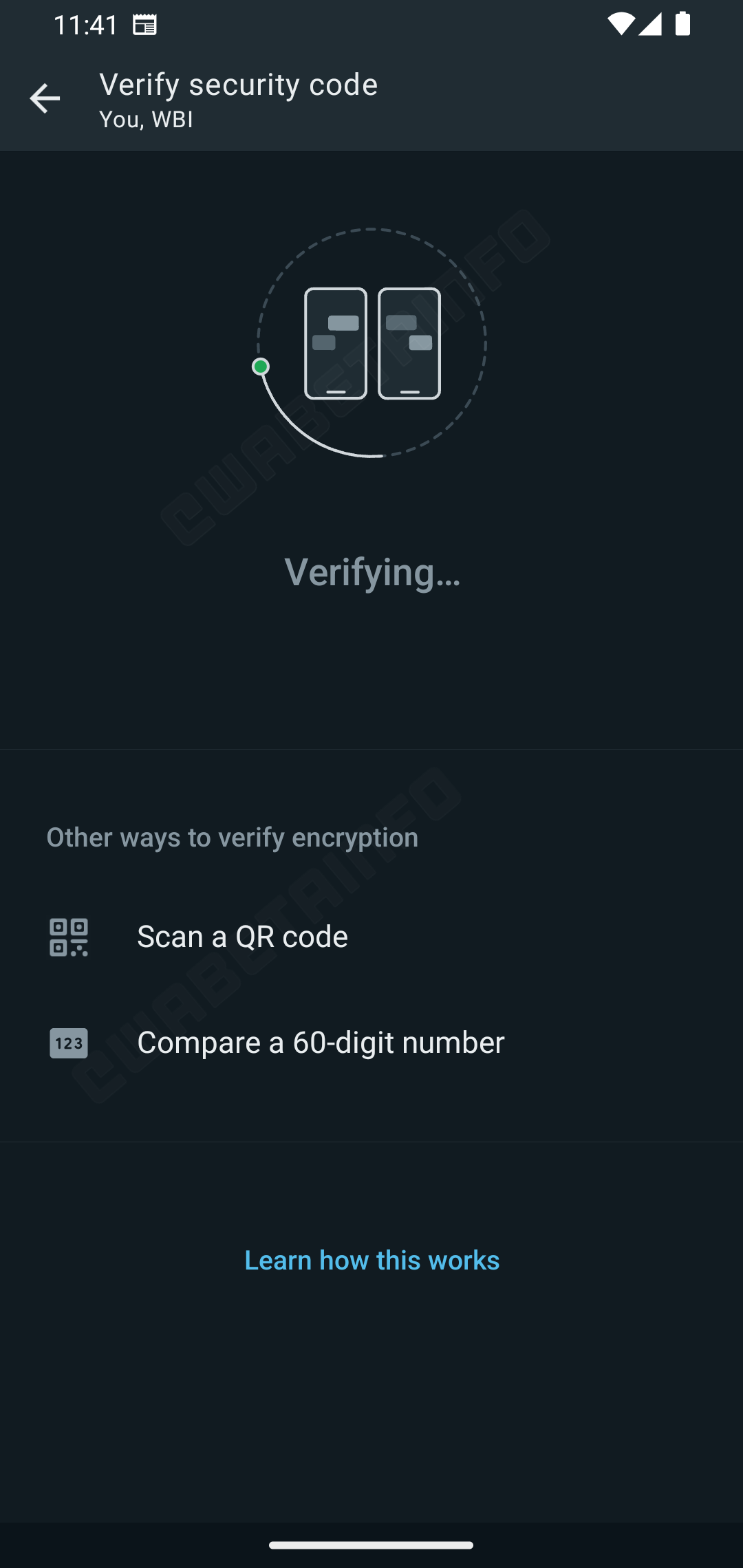
Automated security code verification in development on the most contemporary WhatsApp beta
The messaging app is within the ruin satisfying this promise with beta version 2.23.19.15 of the app on hand on the Play Store, WABetaInfo experiences. Two older versions, 19.13 and 19.14, are also marked properly suited. With this, WhatsApp will get rid of the need for human involvement within the verification direction of. In a technical white paper dedicated to the automation of the direction of, the firm’s engineers snarl that it uses an open-supply, Rust-primarily primarily based auditable key directory (AKD) of the publicly listed keys linked to consumer accounts where anyone can display screen the changes to the keys. Whereas this is able to presumably seem counterintuitive to E2EE, these public keys are handiest feeble to encrypt messages, while the decryption keys live minute to users’ gadgets to compose certain that that privateness.
WhatsApp explains that ragged keys for participant pairs in neighborhood chats must be regenerated whenever even a single participant changes their application, enrolls a unusual application, joins the chat, or leaves it. That’s 4,950 pairs of security verifications for a 100-member chat. Multiply that by the hundreds and hundreds of individuals the exercise of WhatsApp every day, and it is obvious the safety verification scheme strains the firm’s processing resources severely. This unusual key transparency scheme doesn’t replace the manual checks, nonetheless dietary supplements them by allowing anyone consumer in a pair to auto-convey their encryption online page in opposition to the general public AKD, vastly reducing the gathering of checks required between pairs of users. It’s possible you’ll presumably presumably presumably continuously tumble succor on the QR scan or the 60-digit code when you occur to prefer manual verification.
Most severely, WhatsApp already hosts an AKD for all its users, no matter the app version and operating scheme they’re the exercise of. So, it is a matter of time earlier than automated verification rolls out within the stable channel, vastly reducing the strain of security verifications on WhatsApp servers, and automating them with an auditable public directory for all its users.






